Decentralized Identifiers (DIDs)
A Decentralized Identifier (DID) is a unique, self-owned identifier that enables verifiable, secure, and decentralized digital identities. Unlike traditional identifiers (such as emails or usernames), DIDs are not tied to centralized authorities or systems. Instead, they are stored on decentralized networks, giving the user complete control over their identity.
To view types of DID Methods Supported by Hovi, please refer here: Interoperability
How DIDs Work in Hovi
In Hovi’s platform, DIDs play a crucial role in creating, issuing, and verifying verifiable credentials. DIDs allow users, organizations, and systems to interact without relying on centralized identity providers. DIDs are associated with decentralized digital wallets and credentials, ensuring secure exchanges between issuers, holders, and verifiers.
A typical DID looks like this:
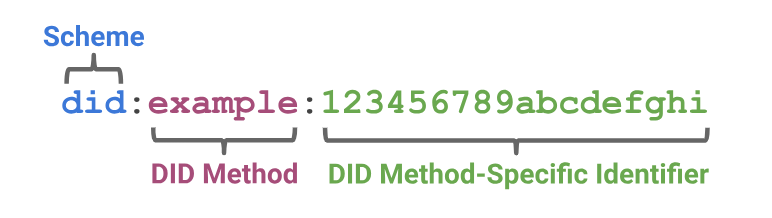
- did: The scheme that indicates it's a Decentralized Identifier.
- example: The method used to generate the DID.
- 123456789abcdefghi: The unique identifier generated for this specific entity.
Key Features of DIDs in Hovi
- Self-Sovereignty: DIDs enable users to fully control their digital identities without being dependent on third-party platforms.
- Interoperability: DIDs are designed to be interoperable across various platforms and services, allowing secure interactions in diverse ecosystems.
- Security & Privacy: DIDs are cryptographically secure and allow users to decide how much information to share with each verifier. For example, a user may provide proof of age without disclosing their full name or address.
- Global Compatibility: DIDs can be used across multiple ecosystems and platforms like Microsoft Entra, EBSI, Polygon, and many more. This flexibility makes them essential for businesses integrating decentralized identity management into their systems.
How DIDs Work with Verifiable Credentials
- Issuer: The entity (e.g., a university or government) issues a verifiable credential using their DID.
- Holder: The user holds the credential in their digital wallet, identified by their own DID.
- Verifier: When verification is required (e.g., proving a diploma's authenticity), the verifier checks the credential using the DID of both the issuer and holder to ensure its validity.
Example in Hovi
Let’s say a government issues a Digital Driver’s License to a user. The government uses their DID to issue the credential. The user receives the credential and stores it in their digital wallet. When the user needs to prove their identity (e.g., when renting a car), they can share their DID and credential with the rental company. The company verifies the credential by checking the government’s DID and the user’s DID to ensure the information is valid and trustworthy.